Automated Security Incident & Vulnerability Management
Automated Security Incident & Vulnerability Management
Role: ServiceNow SecOps Specialist
An organization, a financial services firm, was experiencing a growing volume of security alerts from various tools (SIEM, EDR, endpoint protection). Their Security Operations Center (SOC) team was overwhelmed, manually correlating alerts and responding to incidents. This resulted in a "Mean Time to Respond" (MTTR) of 72 hours for critical incidents, leaving them exposed to prolonged threats.
WHAT WE DECIDED UPON:Implement and integrate ServiceNow Security Incident Response (SIR) and Vulnerability Response (VR) to automate alert ingestion, prioritize threats, and orchestrate security workflows, thereby reducing response times and proactive risk.
ACTION:1. Automated Alert Ingestion: Configured Event Management Connectors to pull alerts from their SIEM (Splunk) and EDR (CrowdStrike) into ServiceNow. Used Alert Rules to automatically generate security incidents for high-fidelity threats.
2. Security Incident Prioritization: Developed custom Risk Calculators within SIR to dynamically assign priority based on asset criticality (from CMDB) and threat intelligence.
3. Orchestrated Response: Designed and implemented Security Playbooks for common incident types (e.g., Phishing, Malware Outbreak). These playbooks included automated actions such as isolating endpoints, blocking malicious IPs via firewall integration, and sending notifications to affected users.
4. Vulnerability Remediation: Integrated Vulnerability Response (VR) with their vulnerability scanner (Qualys). Configured Vulnerability Assignment Rules to automatically create and assign remediation tasks to IT Operations teams based on asset ownership and CVSS scores, streamlining the patching process.
5. Threat Intelligence Integration: Integrated a Threat Intelligence Platform (TIP) to enrich security incidents with real-time threat data, providing analysts with better context.
"Before TRONEXA's work, our SOC team was drowning in alerts and constantly playing catch-up. Their implementation of SIR and VR has transformed our security posture. We now respond to threats with unprecedented speed and precision, and our vulnerability management is no longer a guessing game. It's a game-changer for our cyber resilience."

Liam O'Connell
Chief Information Security Officer (CISO)
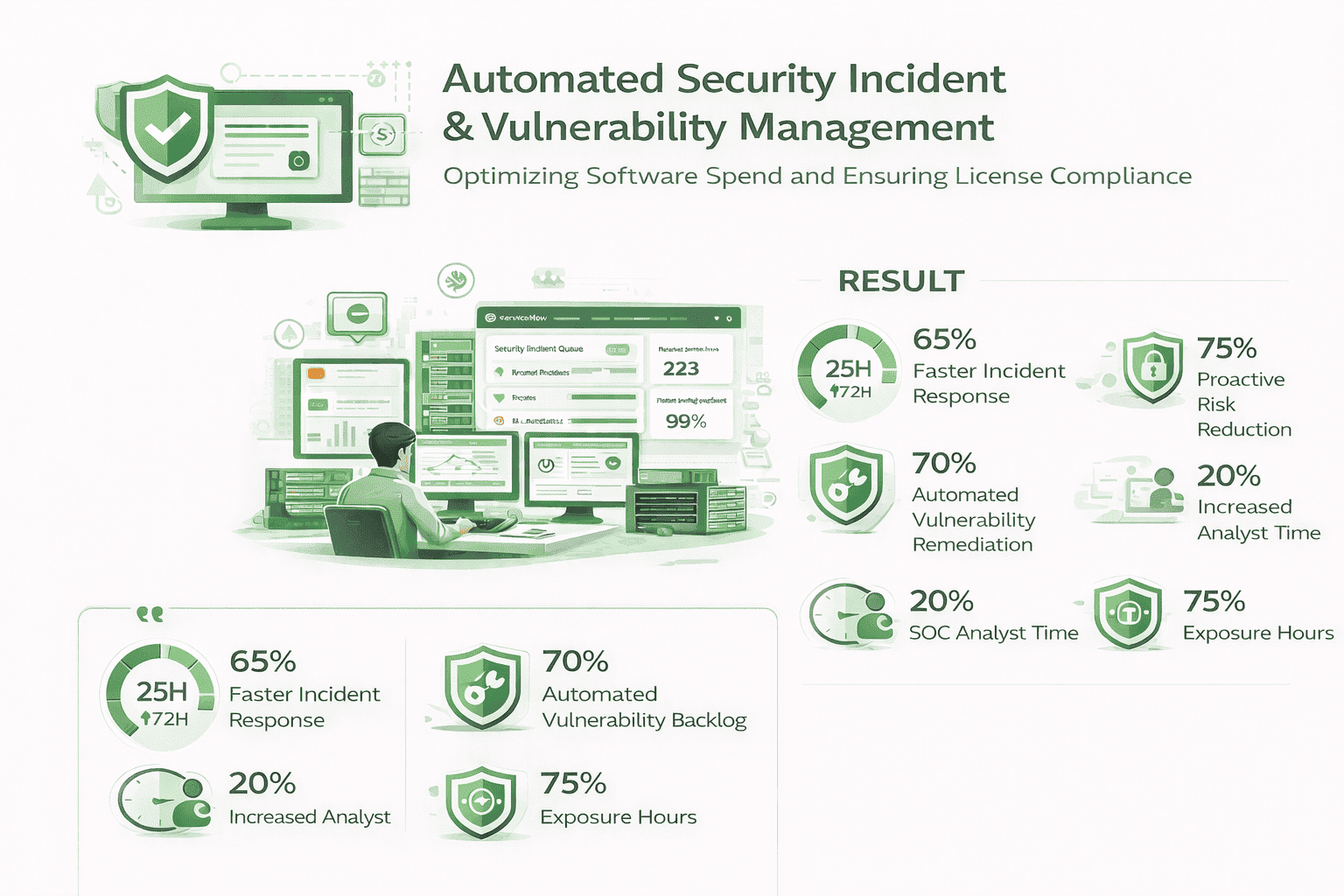
Rapid Response: Reduced the Mean Time to Respond (MTTR) for critical security incidents by 65% (from 72 hours to 25 hours).
Proactive Remediation: Automated 70% of vulnerability remediation task assignments, leading to a 25% reduction in critical vulnerability backlog.
Analyst Efficiency: Freed up 20% of SOC analyst time previously spent on manual correlation and triage, allowing them to focus on advanced threat hunting.
Project information
- Category Security Operations (SecOps)
- ClientSentinel Cyber Solutions
- Project date 14 August, 2023
